Peris.ai Analysis: Brain Cipher Ransomware Attack on Indonesia’s National Data Center
Peris.ai, a group of practitioners with professional experience in cybersecurity, revealed in more detail about the Cipher Brain ransomware that has attacked the Temporary National Data Center since last June 20.
Recently, a shocking incident occurred that resulted in the disruption of immigration services and various other public services. The disruption stemmed from a cyberattack carried out by Brain Cipher Ransomware.
The Pusat Data Nasional (PDN) was the main target of this attack since June 20. The cyberattack has crippled essential services like immigration services, leading to another impact on 210 instantiations. Although some services have been restored, the impact is still felt.
The Badan Siber dan Sandi Negara (BSSN) and related institutions immediately responded to this incident. Emergency measures were taken by sending an assistance team to the data center in Surabaya. The PDNS was built as an alternative because the main Pusat Data Nasional (PDN) is not yet completed.
The responsible party for this attack demanded a ransom of USD 8 million (approximately Rp 131 billion) to restore access to the system.
For context, PDN is managed by Telkom Group through Telkom Sigma. Telkom Indonesia’s Network & IT Solution Director, Herlan Wijanarko, confirmed the ransom demand. However, the compensation process is still under evaluation.
Brain Cipher Ransomware: An Overview
In parallel with the recent events, the Brain Cipher Ransomware is an emerging threat actor currently focusing on organizational targets. The following analysis details the methods, indicators of compromise (IOCs), and tactics used by this ransomware group.
Method of Delivery: Phishing
Brain Cipher Ransomware is delivered primarily through phishing campaigns. These campaigns often use deceptive emails to trick recipients into downloading and executing malicious files.
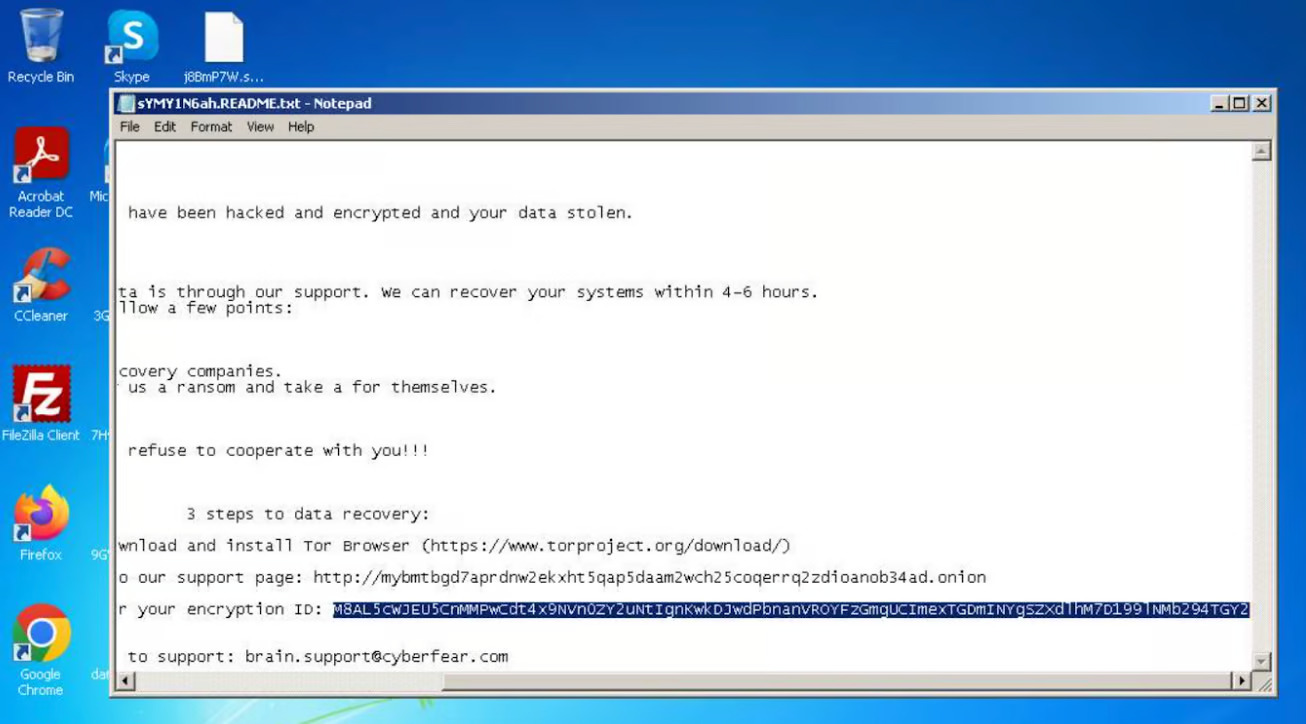
Indicators of Compromise (IOCs)
– MD5: 448f1796fe8de02194b21c0715e0a5f6
SHA1: 935c0b39837319fda571aa800b67d997b79c3198
– SHA256: eb82946fa0de261e92f8f60aa878c9fef9ebb34fdababa66995403b110118b12
– SSDEEP: 3072/5qUpfDT6zT73Ew8Ym9wV9JyknP7SAy
– IP Addresses: 199.232.214.172 (US), 224.0.0.252
– Web: http://mybmtbgd7aprdnw2ekxht5qap5daam2wch25coqerrq2zdioanob34ad.onion
– Email: brain.support@cyberfear.com
– VirusTotal:VirusTotal Link
MITRE ATT&CK
Execution
– T1059.003: Windows Command Shell
– T1204.002: User Execution Malicious File
Privilege Escalation
– T1548.002: Bypass User Account Control
Defense Evasion
– T1548.002: Bypass User Account Control
Credential Access
– T1539: Steal Web Session Cookies
– T1555.003: Credentials from Web Browsers
– T1552.001: Credentials in Files
Discovery
– T1012: Query Registry
– T1082: System Information Discovery
– T1518: Software Discovery
Impact
– T1486: Data Encryption for Impact
Detailed Analysis
The Brain Cipher Ransomware employs sophisticated techniques to infiltrate, propagate, and encrypt data within targeted networks. Its primary delivery method is through phishing emails, which often contain malicious attachments or links leading to malware downloads.
Once inside a network, the ransomware utilizes various tactics to escalate privileges, evade defenses, and gain access to sensitive information. For instance, it uses Windows Command Shell for execution and bypasses user account control for privilege escalation.
The ransomware’s discovery tactics include querying the registry, discovering system information, and software discovery. These actions allow the ransomware to map out the infected environment and identify high-value targets for encryption.
Credential access is a significant aspect of Brain Cipher’s methodology. It steals web session cookies, credentials from web browsers, and credentials stored in files, providing the attackers with the necessary information to further infiltrate the network or exfiltrate data.
Finally, the ransomware’s impact tactic is data encryption, which renders the victim’s data inaccessible until a ransom is paid. This tactic is effective in causing significant disruption to organizational operations, as seen in the recent attack on Indonesia’s National Data Center.
Mitigation and Response
To mitigate the threat posed by Brain Cipher Ransomware and similar attacks, organizations should adopt a multi-layered security approach. This includes:
– Email Security: Implementing robust email security solutions to detect and block phishing attempts.
– User Training: Regularly training employees to recognize and report phishing emails.
– Endpoint Security: Deploying advanced endpoint protection to detect and prevent malware execution.
– Network Segmentation: Segregating critical systems and data to limit the spread of ransomware.
– Backup Solutions: Maintaining regular backups of critical data and ensuring that backups are stored securely and offline.
– Incident Response Planning: Developing and regularly updating incident response plans to ensure a swift and effective response to ransomware attacks.
Enhancing Your Cybersecurity with Peris.ai
As cyber threats continue to evolve, it becomes increasingly important for organizations to stay ahead of potential attacks. Peris.ai offers advanced cybersecurity solutions designed to anticipate and defend against such threats. One such measure is Peris.ai’s Phisland, a sophisticated phishing simulator designed to safeguard your digital frontier.
What is Ganesha – Phisland?
Phisland is a comprehensive phishing simulator that provides your organization with the tools to stay ahead of cyber threats. By simulating phishing attacks via email, websites, and WhatsApp, Phisland helps enhance your team’s security awareness and overall cybersecurity posture.
How does it work?
Realistic Simulations: Phisland offers a suite of realistic phishing simulations that mimic real-world attacks. By tracking user interactions with these simulations, Phisland enables organizations to identify vulnerabilities and opportunities for improvement in real-time.
Enhance Security Awareness: Phisland stands out with its ability to analyze and interpret user responses intelligently. Through advanced algorithms and customizable analytics, Phisland distils vast amounts of data into actionable intelligence, helping organizations create targeted and effective strategies to enhance their security awareness and resilience against cyber threats.
Embrace Phisland to proactively strengthen your cybersecurity measures and protect your organization from potential phishing attacks.
Conclusion
The recent ransomware attack on Indonesia’s National Data Center underscores the escalating threat of ransomware and the profound impact such incidents can have on public services. The emergence of threats like Brain Cipher Ransomware further emphasizes the necessity for robust cybersecurity measures to guard against evolving cyber threats.
Organizations must remain vigilant, continually updating their security practices and staying informed about the latest threat intelligence to effectively combat ransomware attacks.
For comprehensive solutions to enhance your cybersecurity posture and protect against these threats, visit Peris.ai Cybersecurity. Explore our wide range of products and services designed to keep your organization secure in an ever-changing digital landscape. Don’t wait—safeguard your digital assets with Peris.ai today!
About Peris.ai – Cybersecurity
Peris.ai was founded by a group of cybersecurity experts with a mission to connect organizations and independent IT security researchers worldwide. Through comprehensive solutions, Peris.ai aims to create a safer digital environment for all. With a team comprising seasoned cybersecurity professionals, bug researchers, software engineers, and more, Peris.ai is dedicated to innovation and excellence in cybersecurity. The company believes in making cybersecurity a fundamental human right and is committed to continuously enhancing its offerings to provide better security for all. By partnering with organizations and individuals, Peris.ai hopes to contribute to a safer world. Explore how Peris.ai can be your trusted partner in achieving robust cybersecurity by visiting their website today.
This Press Release has also been published on VRITIMES